Massimiliano Gori
on 27 November 2024
In September we introduced Authd, a new authentication daemon for Ubuntu that allows direct integration with cloud-based identity providers for both Ubuntu Desktop and Server. At launch, Authd supports Microsoft Entra ID (formerly Azure Active Directory), making it a useful tool to centralize authentication for both the application and the infrastructure layer.
In large enterprises system administrators often need to deploy and manage applications and their configuration at scale. In this blog we will explore how Cloud-init and Landscape can be used to automate the installation and configuration steps on both private and public clouds.
The content of this blog was also discussed in the following video where you can find a detailed run through of the aforementioned use cases:
Using Entra ID to authenticate into an Ubuntu Server
The high level installation and configuration process for Authd is outlined below:
- [prerequisite] Register an application on EntraID – You can complete this required first step byy following the instructions outlined in Microsoft Documentation, and giving relevant users access to it
- Add authd PPA and install the authd deb – Authd is provided through a supported PPA, which must be added before the package can be installed
- Install the authd-msentraid snap – The Authd deb exposes an API over dbus, which is then consumed by the relevant identity brokers, delivered via a snap package. At the time of writing only the Entra ID snap is available; however, additional identity providers will become available in the coming months. Multiple broker snaps can be used alongside each other, allowing Ubuntu to concurrently support multiple identity providers.
- Set the issuer and client ID in the broker snap config file – This is the minimum configuration set required for the solution to work. However, the broker allows for additional options like setting the allowed email suffixes, home directory structure or timeout
- Configure sshd to use PAM and KbdInteractiveAuthentication – This step will make sure that the relevant PAM module can be used at the moment of login
- Restart services -Restart the service or operating system in order for your changes to take effect
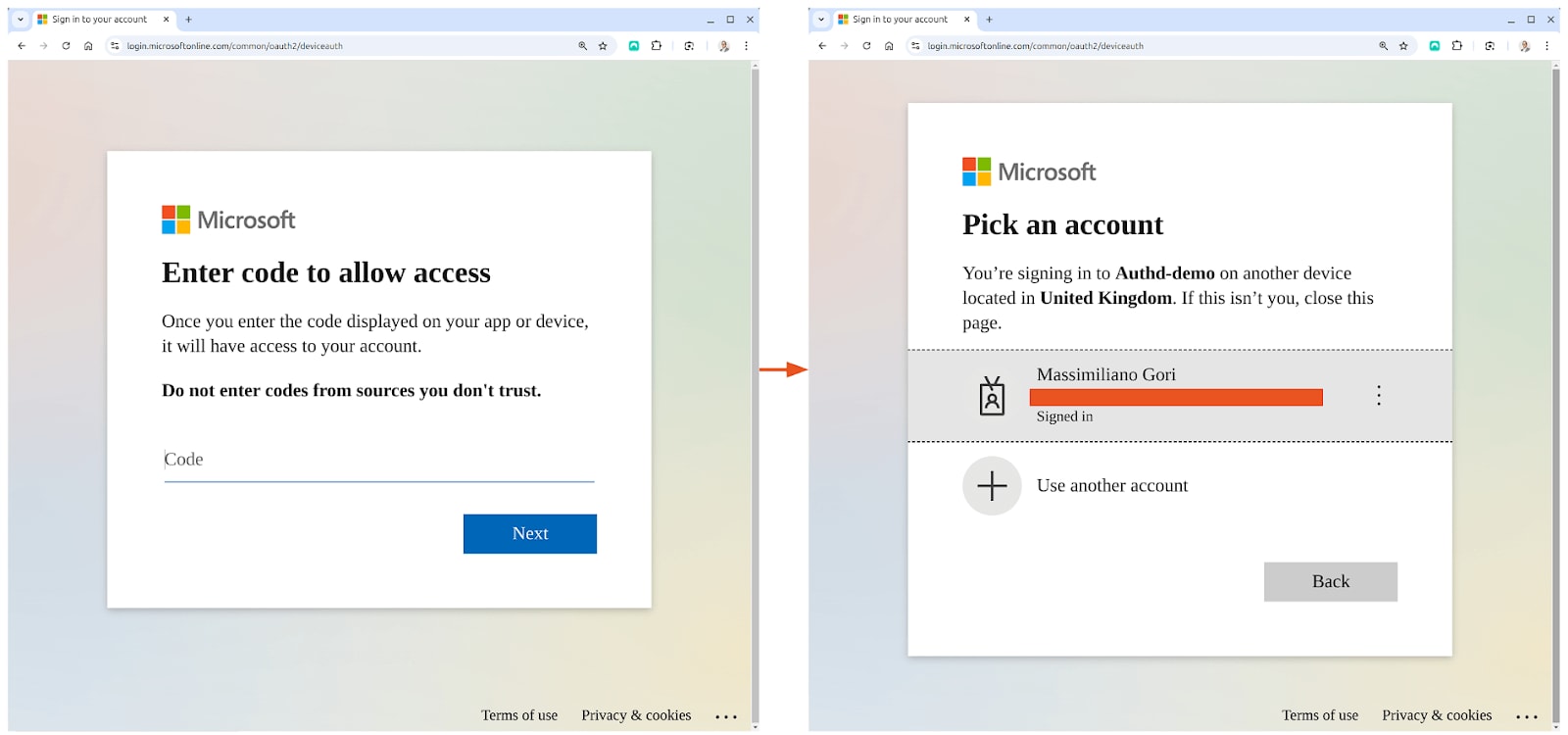
Once all the steps have been completed a Device Authentication option will appear when attempting to log in to the machine via SSH. Upon entering a valid email address you will be presented with a link to the microsoft.com/devicelogin page and a code to validate the identity of the device making the request.
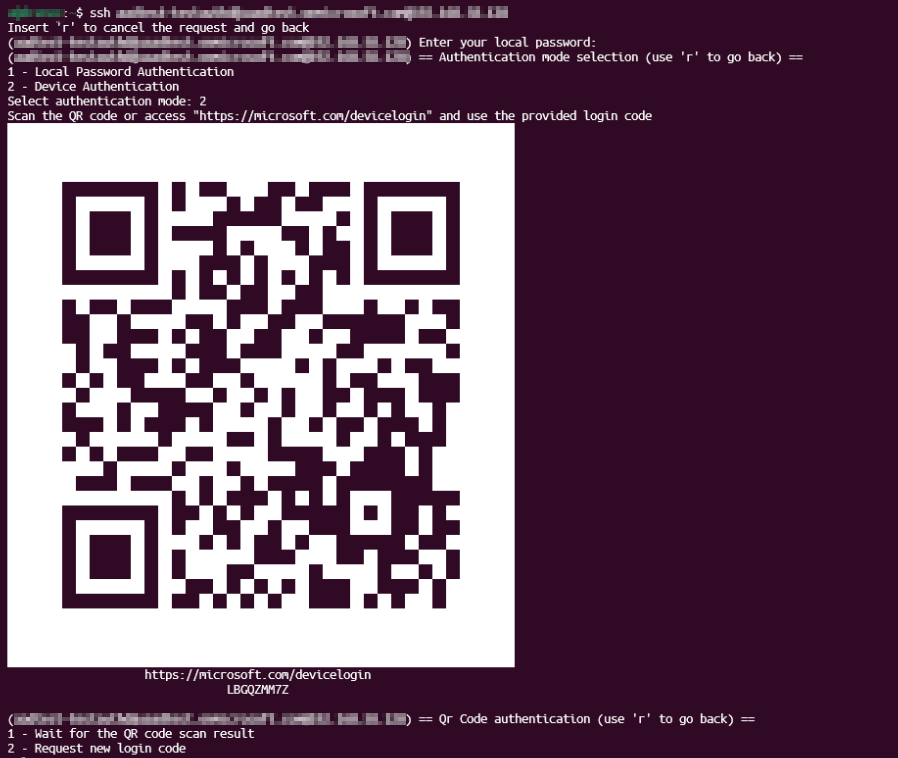
Auth architecture allows you to inherit all the authentication options, device posture and compliance policies you have defined for your Entra ID tenant. There is no extra configuration needed on the cloud side, meaning that even authentication methods like Passkeys and Authenticator are supported out of the box.
Once you visit the devicelogin page you will be served the authentication flow you have configured in your Entra ID tenant.
Deployment automation with Cloud-init
Cloud-init is the industry-standard, multi-distribution method for cross-platform cloud instance initialization. It’s like a setup wizard for your cloud instances, automating the configuration of things like networking, storage, SSH access, and user accounts on first boot. Cloud-init is widely adopted across public clouds, Canonical and other third party system management products.
Below you will find some code snippets which can be added to your existing Cloud-init scripts to install and configure Authd on Ubuntu Servers.
- Update packages and set the application and tenant ID variables – These will be used later on, in the configuration files
# SET OUR VARIABLES
# =================
# Application ID
{% set CLIENT_ID = '3zs4x7w4m7xuk8xkgkycu934y9dvmqu785ca' %}
# Tenant ID
{% set ISSUER_ID = 'f4e2tqd8jg6h92qmxse1nmg535qjm84fbadr' %}
# =========================
# apt update and upgrade.
package_update: true
package_upgrade: true- Add the Authd PPA and install the deb and Entra ID broker snap
# Add authd PPA
apt:
sources:
source1:
source: 'ppa:ubuntu-enterprise-desktop/authd'
# deb and snap install
packages:
- authd
snap:
commands:
- ['install', 'authd-msentraid']- Apply the configuration and restart the services – In this final step we add the necessary configuration to the config files, pointing the broker to our Entraa ID tenant. The services or the host need to be restarted in order for the changes to take effect.
write_files:
- path: /etc/ssh/sshd_config.d/authd.conf
content: |
UsePAM yes
KbdInteractiveAuthentication yes
runcmd:
- sed -i 's|<CLIENT_ID>|{{ CLIENT_ID }}|g; s|<ISSUER_ID>|{{ ISSUER_ID }}|g' /var/snap/authd-msentraid/current/broker.conf
- echo 'ssh_allowed_suffixes = @test.onmicrosoft.com' >> /var/snap/authd-msentraid/current/broker.conf
- sed -i 's/^\(LOGIN_TIMEOUT\t\t\)[0-9]\+/\1360/' /etc/login.defs
- mkdir -p /etc/authd/brokers.d/
- cp /snap/authd-msentraid/current/conf/authd/msentraid.conf /etc/authd/brokers.d/
- snap restart authd-msentraid
- systemctl restart authd
- systemctl restart ssh
- rebootTaking the solution to scale with Landscape
Canonical Landscape is Canonical system management tool available as part of Ubuntu Pro. It allows administrators to manage Ubuntu machines at enterprise scale through a web portal or API, providing controls for:
- software updates and configuration;
- security and compliance auditing and enforcement;
- inventories of software, vulnerabilities, and machines.
Landscape’s self-hosted edition can be run on-premises, or accessed through a software-as-a-service through Canonical’s cloud, with any Ubuntu Pro entitlement. For organizations who want the benefits of a SaaS service, without a multitenant deployment, Canonical provides Managed Landscape. Managed Landscape has an additional cost to account for time spent with Canonical’s Field Engineers, to resiliency and high availability requirements and deploy Landscape to a public cloud of your choosing, or on-premises.
Landscape provides a means to install and configure Authd at scale via Landscape’s remote script execution capability, and can ensure the appropriate packages remain installed over time through the repository and package management capabilities.
Remote script execution
Remote script execution can be used for the initial package installation and for configuration. The script largely follows the cloud-init example earlier. First, set the CLIENT_ID and ISSUER_ID variables, which will be used further down within the script.
#!/bin/bash
CLIENT_ID='1b3d5f7h-i9k0-99xf-425v-56477x8q62xy'
ISSUER_ID='9k8e1c2x-u8g5-71oi-131j-66242u5h10fu'Next, update the repository configuration to retrieve the Authd package from the ppa:ubuntu-enterprise-desktop/authd PPA. Update and upgrade all the packages on the system, and then install the Authd package.
add-apt-repository -y ppa:ubuntu-enterprise-desktop/authd
apt update && apt upgrade -y
apt-get install -y authdAuthd requires the companion authd-msentraid snap package:
snap install authd-msentraidWhile configuration files can be atomically and idempotently updated with tools like augeas and crudini, these extra dependencies are not required. For the purpose of this blog post, we can use sed to update files and echo to amend lines into config files.
The first configuration file which needs to be updated belongs to the authd-msentraid package. The CLIENT_ID and ISSUER_ID get updated within this file using sed replacements. Using echo, the domain(s) running the email service are added in a comma separated manner, without spaces, at the end of the default configuration file.
sed -i "s|<CLIENT_ID>|$CLIENT_ID|g; s|<ISSUER_ID>|$ISSUER_ID|g" /var/snap/authd-msentraid/current/broker.conf
echo 'ssh_allowed_suffixes = @uaadtest.onmicrosoft.com,@ubuntu.com' >> /var/snap/authd-msentraid/current/broker.confNext, SSH configurations for Authd need to be applied. The configuration file does not yet exist, so we will use the touch command to create the file before appending 2 lines into it:
touch /etc/ssh/sshd_config.d/authd.conf
echo "UsePAM yes" >> /etc/ssh/sshd_config.d/authd.conf
echo "KbdInteractiveAuthentication yes" >> /etc/ssh/sshd_config.d/authd.confThe login timeout may need to be extended to accommodate the accessibility needs of all users. The default timeout of 30 seconds may be too short, and extending it to 360 seconds may be more comfortable. This update is also performed using sed:
sed -i 's/^\(LOGIN_TIMEOUT\t\t\)[0-9]\+/\1360/' /etc/login.defsLastly, an msentraid.conf configuration file provided by the authd-msentraid snap package needs to be copied to a directory which does not yet exist: /etc/authd/brokers.d/
mkdir -p /etc/authd/brokers.d/
cp /snap/authd-msentraid/current/conf/authd/msentraid.conf /etc/authd/brokers.d/The authd, authd-msentraid, and ssh services all need to be restarted to apply these changes:
systemctl restart authd
snap restart authd-msentraid
systemctl restart sshIt may be prudent to reboot, if any deb archive updates require a machine restart. The complete script appears as follows:
#!/bin/bash
CLIENT_ID='1b3d5f7h-i9k0-99xf-425v-56477x8q62xy'
ISSUER_ID='9k8e1c2x-u8g5-71oi-131j-66242u5h10fu'
add-apt-repository -y ppa:ubuntu-enterprise-desktop/authd
apt update && apt upgrade -y
apt-get install -y authd
snap install authd-msentraid
sed -i "s|<CLIENT_ID>|$CLIENT_ID|g; s|<ISSUER_ID>|$ISSUER_ID|g" /var/snap/authd-msentraid/current/broker.conf
echo 'ssh_allowed_suffixes = @uaadtest.onmicrosoft.com,@ubuntu.com' >> /var/snap/authd-msentraid/current/broker.conf
touch /etc/ssh/sshd_config.d/authd.conf
echo "UsePAM yes" >> /etc/ssh/sshd_config.d/authd.conf
echo "KbdInteractiveAuthentication yes" >> /etc/ssh/sshd_config.d/authd.conf
sed -i 's/^\(LOGIN_TIMEOUT\t\t\)[0-9]\+/\1360/' /etc/login.defs
mkdir -p /etc/authd/brokers.d/
cp /snap/authd-msentraid/current/conf/authd/msentraid.conf /etc/authd/brokers.d/
# systemctl restart authd
# snap restart authd-msentraid
# systemctl restart ssh
rebootRepository and package management
At the time of this writing, applying repository mirror profiles is limited to self-hosted Landscape installations. It is possible to mirror the Authd PPA into Landscape, or configure the machines managed by Landscape to retrieve the Authd package directly from the PPA instead of Landscape’s mirror.
Profiles in Landscape can be thought of as a collection of policies, and these are applied to selections of machines in Landscape based on a combination of Access Groups, and Tags.
The combination of remote script execution across a selection of machines by Access Group and Tag, coupled with the optional repository and package management, ensures your Authd rollout is successful at enterprise scale.



